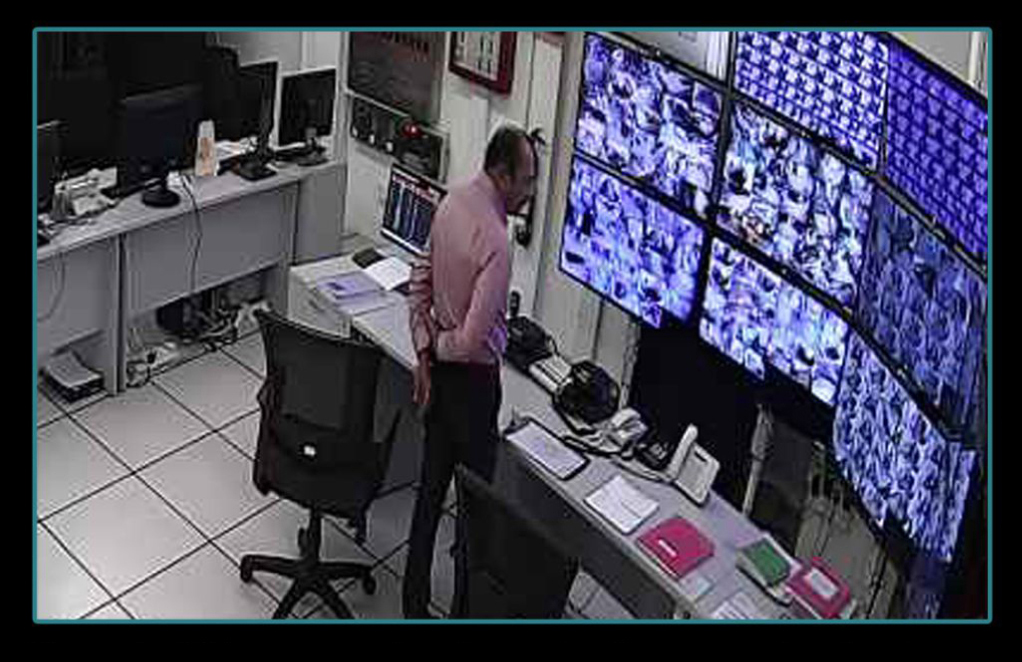
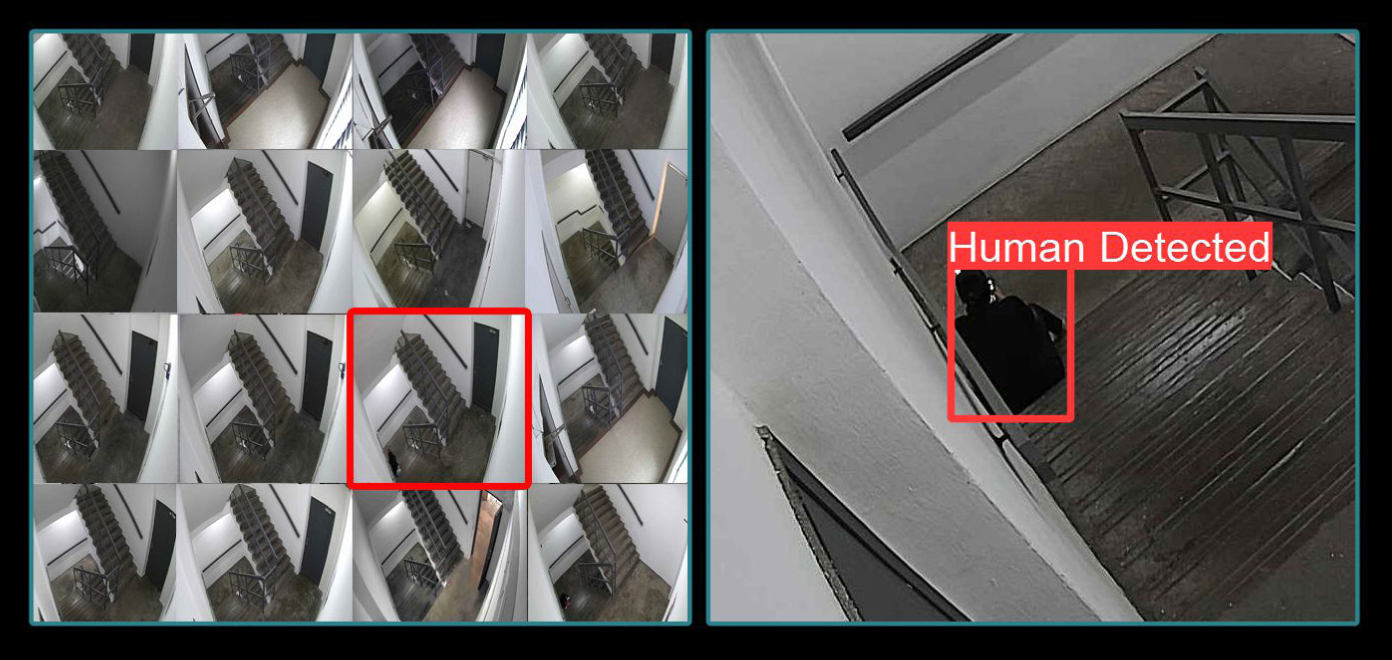
ADA's practical vision analytics accurately detects human presence
in any CCTV scene without complex configurations or additional hardware.
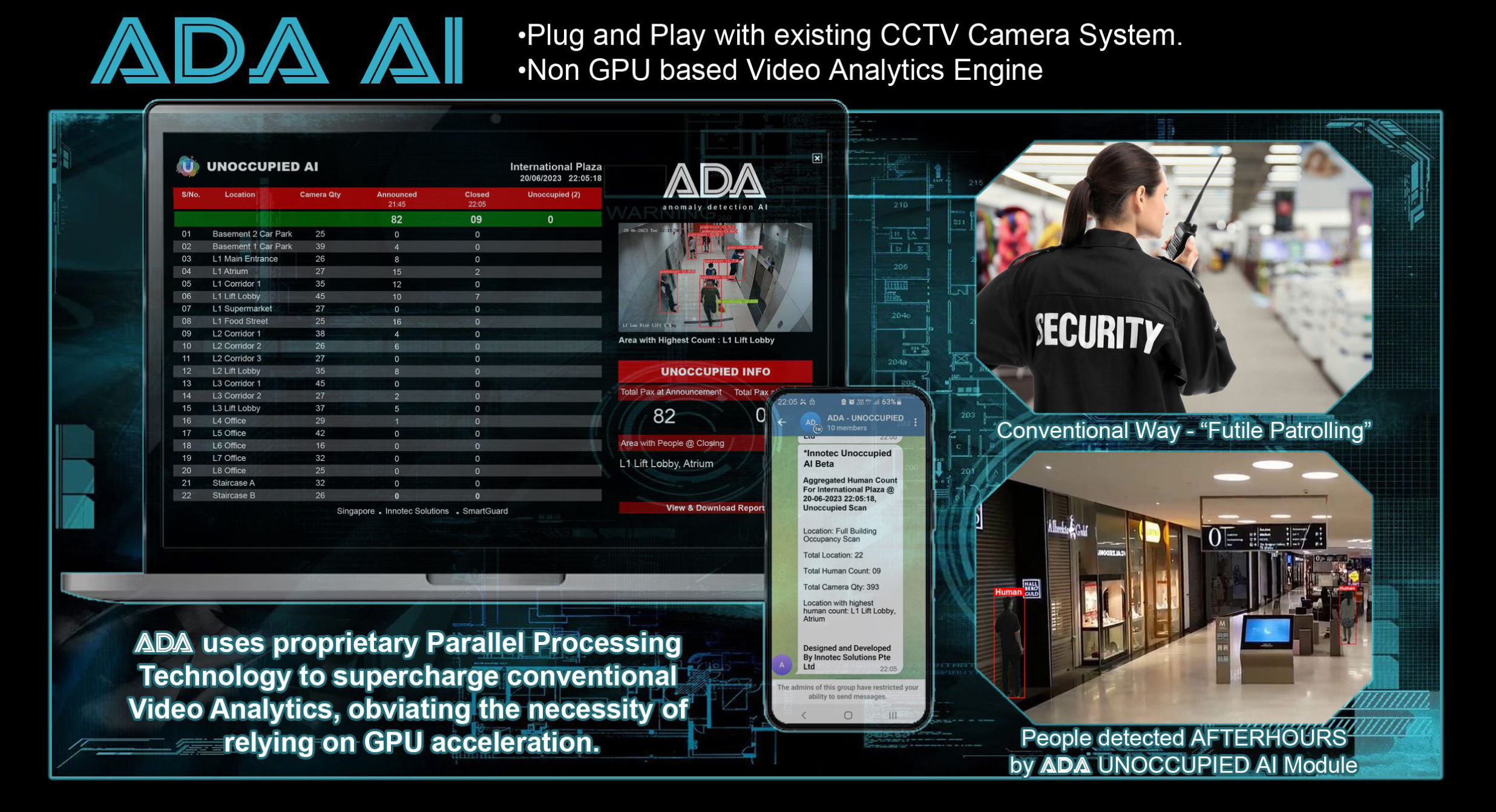
Empowers security managers with real-time human count and location statistics, ensuring secure building clearance after closing time.
Integrates with mobile phones provides instant alerts on human presence and detected locations for swift action.
Streamlines security operations by eliminating the need for labor-intensive physical checks.
Enhances building occupancy monitoring through consolidated real-time information on a single screen.
ADA's intelligent AI sets new standards for smart security, optimizing surveillance and enhancing efficiency in protecting occupants and premises.
Conventional patrolling for ensuring premises clearance, especially in large areas, can indeed be inefficient and prone to several challenges.
Some of the common inefficiencies include:
Limited Coverage
Physical patrols have limitations in terms of covering vast or remote areas effectively, resulting in blind spots which are vulnerable to unauthorized access.
Predictable Schedule
Traditional patrols often follow a fixed schedule, allowing potential intruders to time their actions/entry accordingly.
Human Error
Physical patrols are subjected to human errors, such as overlooking certain areas or leaving vulnerabilities unaddressed.
Resources Required
A dedicated security team is costly to upkeep, especially for small or medium-sized business or properties. By digitalizing prowling activities, manpower can be repurposed for cognitive activities.
Fatigue and Alertness
Security officers may experience fatigue during long shifts, leading to decreased alertness and them being less vigilant against threats.
Lack of Real-Time Information
Conventional patrols may not provide real-time data on incidents or potential threats, making it challenging for incident response and management.
Limited Coverage
Physical patrols have limitations in terms of covering vast or remote areas effectively, resulting in blind spots which are vulnerable to unauthorized access.
Predictable Schedule
Traditional patrols often follow a fixed schedule, allowing potential intruders to time their actions/entry accordingly.
Human Error
Physical patrols are subjected to human errors, such as overlooking certain areas or leaving vulnerabilities unaddressed.
Resources Required
A dedicated security team is costly to upkeep, especially for small or medium-sized business or properties. By digitalizing prowling activities, manpower can be repurposed for cognitive activities.
Fatigue and Alertness
Security officers may experience fatigue during long shifts, leading to decreased alertness and them being less vigilant against threats.
Lack of Real-Time Information
Conventional patrols may not provide real-time data on incidents or potential threats, making it challenging for incident response and management.
Conventional patrolling for ensuring premises clearance, especially in large areas, can indeed be inefficient and prone to several challenges.
Some of the common inefficiencies include:
Limited Coverage
Physical patrols have limitations in terms of covering vast or remote areas effectively, resulting in blind spots which are vulnerable to unauthorized access.
Predictable Schedule
Traditional patrols often follow a fixed schedule, allowing potential intruders to time their actions/entry accordingly.
Human Error
Physical patrols are subjected to human errors, such as overlooking certain areas or leaving vulnerabilities unaddressed.
Resources Required
A dedicated security team is costly to upkeep, especially for small or medium-sized business or properties. By digitalizing prowling activities, manpower can be repurposed for cognitive activities.
Fatigue and Alertness
Security officers may experience fatigue during long shifts, leading to decreased alertness and them being less vigilant against threats.
Lack of Real-Time Information
Conventional patrols may not provide real-time data on incidents or potential threats, making it challenging for incident response and management.
Limited Coverage
Physical patrols have limitations in terms of covering vast or remote areas effectively, resulting in blind spots which are vulnerable to unauthorized access.
Predictable Schedule
Traditional patrols often follow a fixed schedule, allowing potential intruders to time their actions/entry accordingly.
Human Error
Physical patrols are subjected to human errors, such as overlooking certain areas or leaving vulnerabilities unaddressed.
Resources Required
A dedicated security team is costly to upkeep, especially for small or medium-sized business or properties. By digitalizing prowling activities, manpower can be repurposed for cognitive activities.
Fatigue and Alertness
Security officers may experience fatigue during long shifts, leading to decreased alertness and them being less vigilant against threats.
Lack of Real-Time Information
Conventional patrols may not provide real-time data on incidents or potential threats, making it challenging for incident response and management.
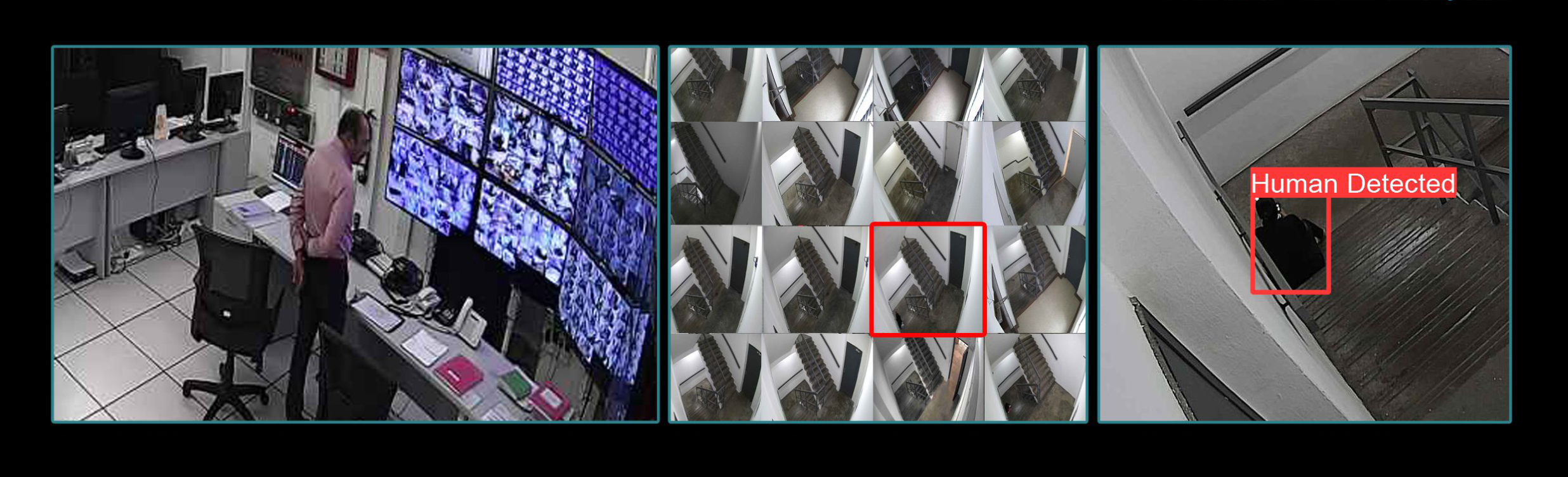
Security Officer scanning through all screens to check.
Conventional way of checking is, "Screen by Screen."
Conventional way of checking is, "Screen by Screen."
ADA Detects human and their location, automatically update to ADA Command,
and sends alerts to officers on the ground via their mobile apps.
and sends alerts to officers on the ground via their mobile apps.
Ada unoccupied ai for patrolling after closing hours offers several significant advantages for ensuring the security and safety of premises during the times when human presences may be limited or unavailable.
Here are some reasons why ADA is particularly useful for patrolling after closing hours:
1. 24/7 Monitoring: ADA-powered surveillance systems can provide continuous monitoring and analysis of security cameras and sensors, ensuring round-the-clock vigilance. This is crucial during closing hours when human patrols might not be present.
2. Real-Time Alerts: ADA can quickly detect and raise alerts for potential security breaches or suspicious activities. This allows for immediate response, either from on-site security personnel or remote monitoring teams.
3. Cost-Effective Solution: Employing ADA-based patrolling during closing hours can be more cost-effective compared to edge based processing technology or even having a dedicated human security team on-site during those hours. It reduces the need for hiring additional personnel for night shifts.
4. Enhanced Detection Capabilities: ADA can be trained to recognize specific patterns or anomalies that might indicate unauthorized access, break-ins, or other security threats. It can detect and track objects or individuals, making it easier to identify potential risks.
5. Reduced False Alarms: ADA can differentiate between regular activities, such as wildlife or environmental changes, and genuine security threats. This helps in reducing false alarms, which can be time-consuming and costly to investigate.
6. Immediate Response: ADA can trigger automated responses, such as notifying security personnel, or sending alerts to key personnels, ensuring quick action in case of any security breach.
7. Multi-Site Monitoring: ADA can be deployed to monitor multiple sites or buildings simultaneously, making it an efficient solution for organizations with several locations or properties.
8. Continuous Learning: ADA can continuously learn from data and improve their detection capabilities over time, staying up-to-date with the latest security trends and threats.
9. Remote Access: ADA-powered systems can be accessed remotely through secure channels, allowing security personnel or management to monitor the premises from anywhere, enabling faster decision-making.
10. Deterrent Effect: The presence of ADA-powered surveillance systems can act as a deterrent to potential intruders or criminals, reducing the likelihood of security incidents during closing hours.
1. 24/7 Monitoring: ADA-powered surveillance systems can provide continuous monitoring and analysis of security cameras and sensors, ensuring round-the-clock vigilance. This is crucial during closing hours when human patrols might not be present.
2. Real-Time Alerts: ADA can quickly detect and raise alerts for potential security breaches or suspicious activities. This allows for immediate response, either from on-site security personnel or remote monitoring teams.
3. Cost-Effective Solution: Employing ADA-based patrolling during closing hours can be more cost-effective compared to edge based processing technology or even having a dedicated human security team on-site during those hours. It reduces the need for hiring additional personnel for night shifts.
4. Enhanced Detection Capabilities: ADA can be trained to recognize specific patterns or anomalies that might indicate unauthorized access, break-ins, or other security threats. It can detect and track objects or individuals, making it easier to identify potential risks.
5. Reduced False Alarms: ADA can differentiate between regular activities, such as wildlife or environmental changes, and genuine security threats. This helps in reducing false alarms, which can be time-consuming and costly to investigate.
6. Immediate Response: ADA can trigger automated responses, such as notifying security personnel, or sending alerts to key personnels, ensuring quick action in case of any security breach.
7. Multi-Site Monitoring: ADA can be deployed to monitor multiple sites or buildings simultaneously, making it an efficient solution for organizations with several locations or properties.
8. Continuous Learning: ADA can continuously learn from data and improve their detection capabilities over time, staying up-to-date with the latest security trends and threats.
9. Remote Access: ADA-powered systems can be accessed remotely through secure channels, allowing security personnel or management to monitor the premises from anywhere, enabling faster decision-making.
10. Deterrent Effect: The presence of ADA-powered surveillance systems can act as a deterrent to potential intruders or criminals, reducing the likelihood of security incidents during closing hours.
Disclaimer:
While ADA is highly advantageous for patrolling after closing hours, it's essential to maintain a balanced approach to security. Integrating ADA with human security measures can provide a comprehensive and robust security solution, ensuring the safety of the premises and its occupants at all times.
Ada unoccupied ai for patrolling after closing hours offers several significant advantages for ensuring the security and safety of premises during the times when human presences may be limited or unavailable.
Here are some reasons why ADA is particularly useful for patrolling after closing hours:
1. 24/7 Monitoring: ADA-powered surveillance systems can provide continuous monitoring and analysis of security cameras and sensors, ensuring round-the-clock vigilance. This is crucial during closing hours when human patrols might not be present.
2. Real-Time Alerts: ADA can quickly detect and raise alerts for potential security breaches or suspicious activities. This allows for immediate response, either from on-site security personnel or remote monitoring teams.
3. Cost-Effective Solution: Employing ADA-based patrolling during closing hours can be more cost-effective compared to edge based processing technology or even having a dedicated human security team on-site during those hours. It reduces the need for hiring additional personnel for night shifts.
4. Enhanced Detection Capabilities: ADA can be trained to recognize specific patterns or anomalies that might indicate unauthorized access, break-ins, or other security threats. It can detect and track objects or individuals, making it easier to identify potential risks.
5. Reduced False Alarms: ADA can differentiate between regular activities, such as wildlife or environmental changes, and genuine security threats. This helps in reducing false alarms, which can be time-consuming and costly to investigate.
6. Immediate Response: ADA can trigger automated responses, such as notifying security personnel, or sending alerts to key personnels, ensuring quick action in case of any security breach.
7. Multi-Site Monitoring: ADA can be deployed to monitor multiple sites or buildings simultaneously, making it an efficient solution for organizations with several locations or properties.
8. Continuous Learning: ADA can continuously learn from data and improve their detection capabilities over time, staying up-to-date with the latest security trends and threats.
9. Remote Access: ADA-powered systems can be accessed remotely through secure channels, allowing security personnel or management to monitor the premises from anywhere, enabling faster decision-making.
10. Deterrent Effect: The presence of ADA-powered surveillance systems can act as a deterrent to potential intruders or criminals, reducing the likelihood of security incidents during closing hours.
1. 24/7 Monitoring: ADA-powered surveillance systems can provide continuous monitoring and analysis of security cameras and sensors, ensuring round-the-clock vigilance. This is crucial during closing hours when human patrols might not be present.
2. Real-Time Alerts: ADA can quickly detect and raise alerts for potential security breaches or suspicious activities. This allows for immediate response, either from on-site security personnel or remote monitoring teams.
3. Cost-Effective Solution: Employing ADA-based patrolling during closing hours can be more cost-effective compared to edge based processing technology or even having a dedicated human security team on-site during those hours. It reduces the need for hiring additional personnel for night shifts.
4. Enhanced Detection Capabilities: ADA can be trained to recognize specific patterns or anomalies that might indicate unauthorized access, break-ins, or other security threats. It can detect and track objects or individuals, making it easier to identify potential risks.
5. Reduced False Alarms: ADA can differentiate between regular activities, such as wildlife or environmental changes, and genuine security threats. This helps in reducing false alarms, which can be time-consuming and costly to investigate.
6. Immediate Response: ADA can trigger automated responses, such as notifying security personnel, or sending alerts to key personnels, ensuring quick action in case of any security breach.
7. Multi-Site Monitoring: ADA can be deployed to monitor multiple sites or buildings simultaneously, making it an efficient solution for organizations with several locations or properties.
8. Continuous Learning: ADA can continuously learn from data and improve their detection capabilities over time, staying up-to-date with the latest security trends and threats.
9. Remote Access: ADA-powered systems can be accessed remotely through secure channels, allowing security personnel or management to monitor the premises from anywhere, enabling faster decision-making.
10. Deterrent Effect: The presence of ADA-powered surveillance systems can act as a deterrent to potential intruders or criminals, reducing the likelihood of security incidents during closing hours.
Disclaimer:
While ADA is highly advantageous for patrolling after closing hours, it's essential to maintain a balanced approach to security. Integrating ADA with human security measures can provide a comprehensive and robust security solution, ensuring the safety of the premises and its occupants at all times.
Disclaimer:
While ADA is highly advantageous for patrolling after closing hours, it's essential to maintain a balanced approach to security. Integrating ADA with human security measures can provide a comprehensive and robust security solution, ensuring the safety of the premises and its occupants at all times.